Article: How to protect files with a password?
Introduction.
In the modern world, information is valuable. People make fortunes selling and buying nothing but information. Business secrets are guarded sometimes better than military ones.
On the other hand, private and business information becomes even more vulnerable. For example, a computer connected to the internet can be attacked by hackers, and, as a result, sensitive files may be stolen. Sometimes they are more important, sometimes less, but in general nobody wants to see personal files appear on the internet.
But hackers and viruses are not the only hazard to your privacy. If you share your computer with other people, your files can be made available to those people relatively easy, even if you use different usernames to login.
However, it is possible to protect your privacy both from other people that use the computer and from network threats. You can encrypt files with a tool like CryptoExpert 2008 Pro.
Step 1: Download and install the program.
Download CryptoExpert 2008 Pro to a known location. Run setup and follow on-screen instructions to install the application.
Step 2: Start the program. Create new encrypted container.
Launch CryptoExpert 2008 Pro. The program shows its main window that is similar to the usual layout of file managers. The windows has three panes that can be used for browsing your disks.
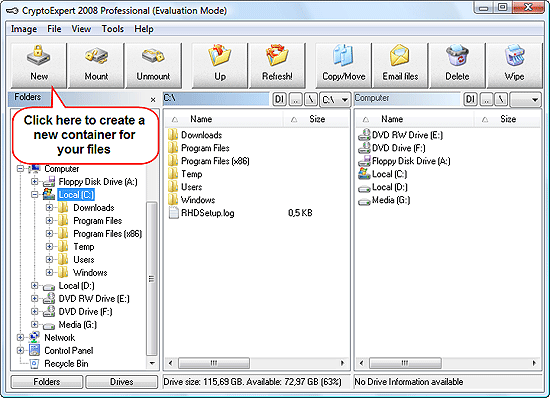
Click "New" on the toolbar. This will launch the image creator wizard:
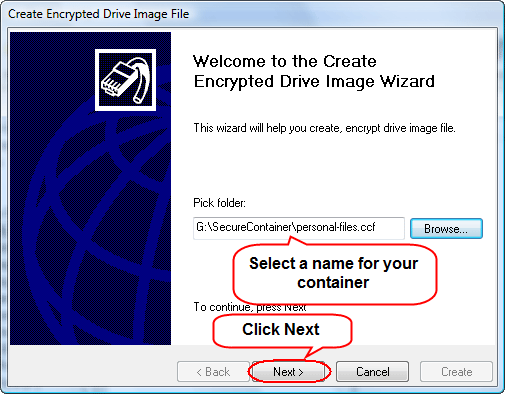
First, decide where you keep your containers with sensitive files.
CryptoExpert 2008 Pro keeps all encrypted files inside special files called containers. The containers cannot be hacked or decrypted, unless you enter correct passwords to mount them. Containers look just like ordinary files, and there's no way to learn about their contents without passwords.
You can use "Browse" to browse to the folder where you want to keep your container files. Enter some filename for your container. Then click "Next".
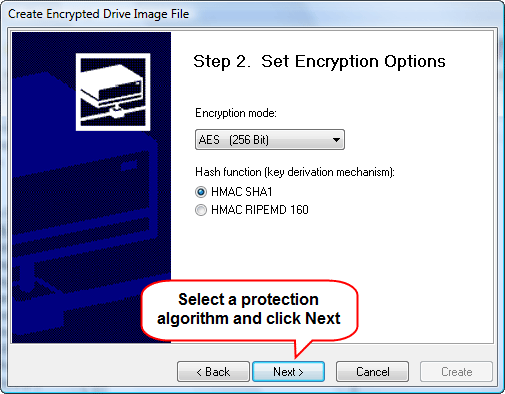
The wizard offers you a number of encryption modes. Defaults are safe, but if you have some special protection in mind, just choose it from the dropdown list. CryptoExpert 2008 Pro supports AES, Blowfish, CAST, 3DES encryption algorithms that are among strongest and most efficient ones.
Click "Next".
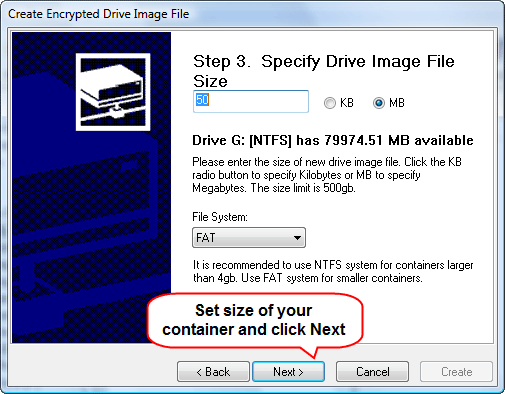
Here you can set size of your container. Size depends on how many files you want to save inside the container, and on how big they are. If you intend keeping only several important documents, 50 MB should be enough. So, let's proceed by clicking "Next".
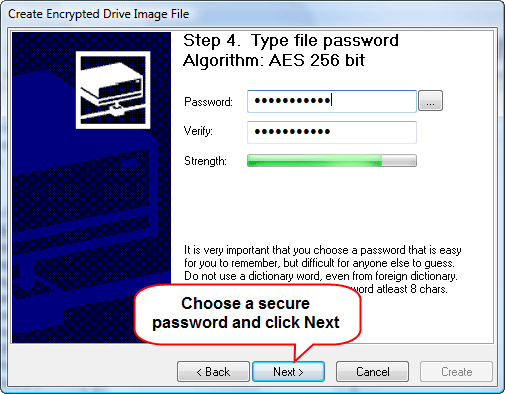
Now the wizard asks for a password. This password will be used to mount the encrypted container (i.e. to access protected files), so you should be able to remember it later somehow. Most people write their passwords down, which is not secure. But then, if you are not sure that you remember the password, you may encode it, or protect by another method. It is not recommended to save passwords in a plain text file on the same computer, though.
The wizards checks your password and determines its strength (see the green bar). If you want your files be safe, don't enter simple words. Combine capital letters with numbers and lowercase letters to achieve better protection.
Once satisfied with your password, enter it once again into the "Verify" field and click "Next".
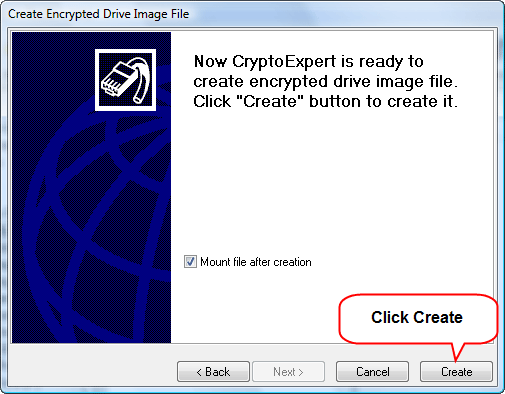
Everything is ready now to create a secure container. Click "Create".
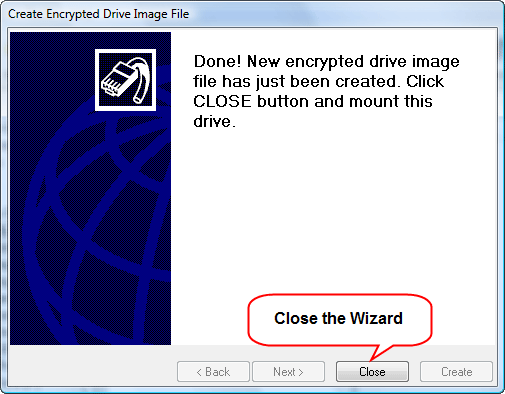
And close the wizard.
Step 3: Mount the container. Protect your files.
We get back to the program window.
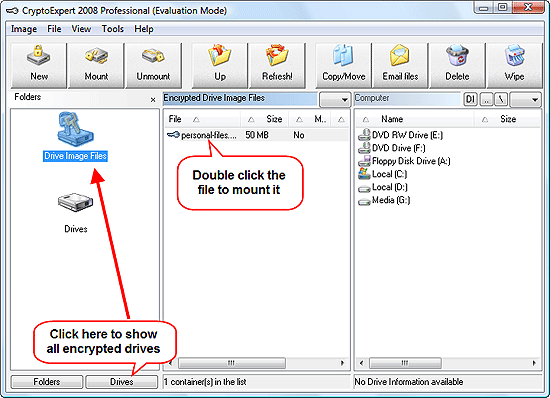
Click "Drives" below to list all drives on your system, select "Drive Image Files" in the first column. In the second one, you will see the created container. Double-click it. The program prompts you to enter your password.
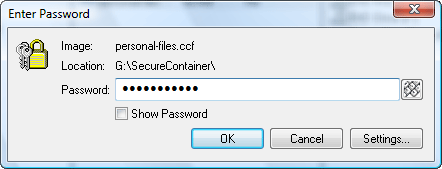
Do it, then click "OK". CryptoExpert 2008 Pro will report that the drive has been successfully mounted. Now you can access it from any application, including Windows Explorer, Microsoft Word, or any other one.
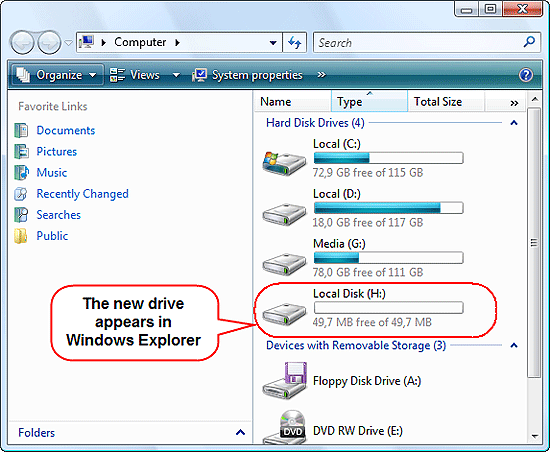
As you copy files to the protected drive, they are automatically encrypted "on the fly". If you access them with some program, they are decrypted. The process is transparent to the user, so you can work with the protected drive just like with an ordinary one. Move your important files there to protect them from possible hazards.
When you finished working with sensitive data, right-click the CryptoExpert 2008 Pro icon in the system tray (near clocks) and choose to unmount the container. The new drive will disappear and won't be accessible until you choose mount it again and enter your password. Its contents will remain unknown to any other user on the computer, as well as to viruses/hackers. Strong protection algorithms guarantee that the container can't be hacked or decrypted by using brute-force attack and other password cracking methods. However, most password crackers start probing with a dictionary attack, so don't set a simple word as your password, as it can be discovered in a few seconds.
- Firewall and Intrusion Detection
- Network/Protocol Analyzer
- Network Scanner
- Privacy and Anonymity
- Whois and TraceRoute
- Network Utilities, Suits, Toolkits
- Network Monitor
- Network Traffic Accounting
- Network Inventory
- Remote Control
- File and Disk Encryption
- File and Password Recovery
- Keylogger and AntiKeylogger
- Email Tools
All Categories
Best Recent Downloads
-
PA Server Monitor Ultra
Agentless distributed monitoring of servers and devices
-
GFI WebMonitor - Standalone Proxy Version
Internet monitoring and web security for SMBs
-
GFI LANguard Network Security Scanner
Network vulnerability management solution.
-
Nsauditor Network Security Auditor
Scan and monitor network.Over 45 net tools.
-
10-Strike Network Inventory Explorer
Monitor network computer inventory
-
Network Administrator's Toolkit
Inventory user PCs and monitor servers
-
Net Monitor for Employees
See their screens and take a control.
-
SpotAuditor
Recovers MSN,IE,Outlook,ICQ,Ras,Ftp passwords
-
Alchemy Eye
Server monitoring tool
-
NetResident
Network content monitor
-
Advanced Host Monitor
Award-winning network monitoring software
-
Network Inventory Reporter
inventory software
-
SpotIE Password Recovery
SpotIE recovers Internet Explorer passwords.
-
Asset Tracker for Networks
Inventory network workstations, build reports
-
SpotMSN Password Recover
Recovers MSN messenger and Live passwords.
-
Accent OFFICE Password Recovery
How to break passwords in Office / OpenOffice
-
East-Tec Eraser 2008
Keep what you do on your computer to yourself
-
Security Task Manager
Enhanced Process Viewer that protects your PC
-
NetInfo
A full-featured network toolkit.
-
SpotFTP Password Recover
Recovers FTP passwords stored in computers.
-
Free IP Scanner
A very fast IP scanner and port scanner.

 Product Page
Product Page